Throwback Attack: Chinese hackers steal plans for the F-35 fighter in a supply chain heist | Industrial Cybersecurity Pulse | Industrial Cybersecurity Pulse

Enterprise data breach: causes, challenges, prevention, and future directions - Cheng - 2017 - WIREs Data Mining and Knowledge Discovery - Wiley Online Library
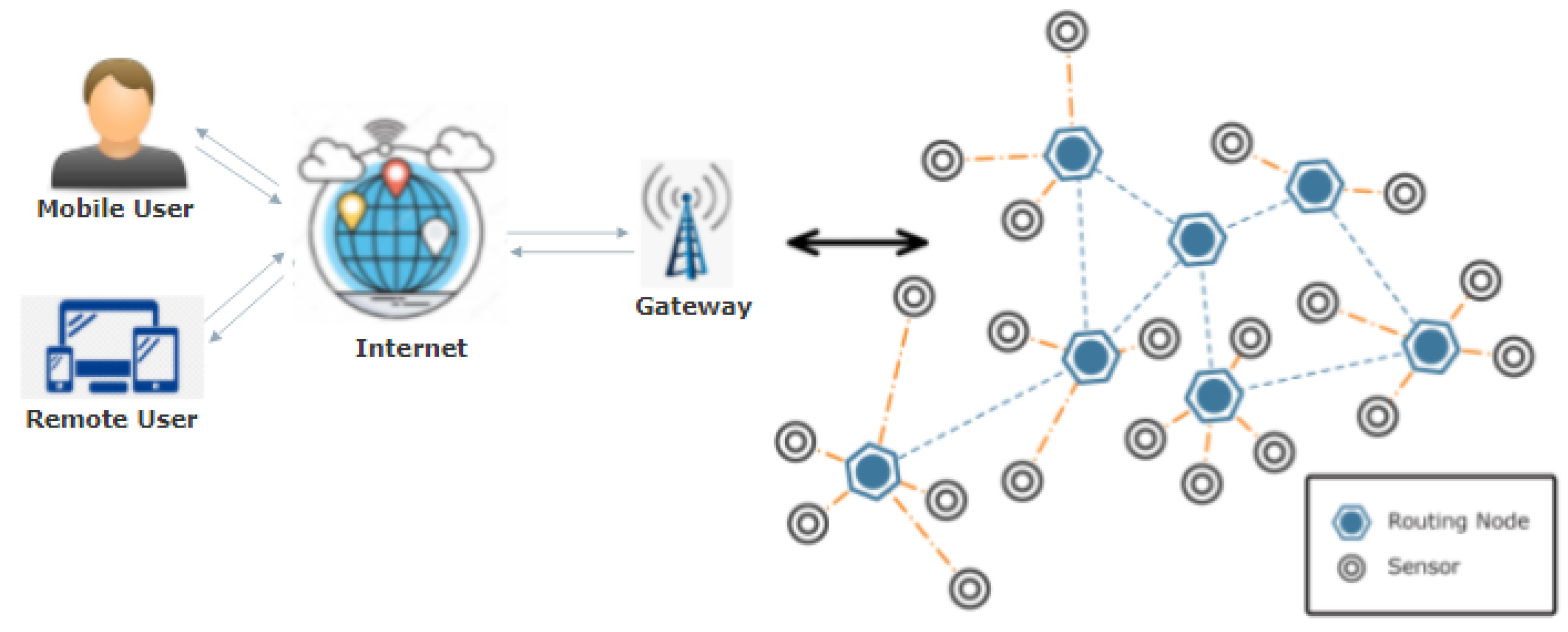
Sensors | Free Full-Text | Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review
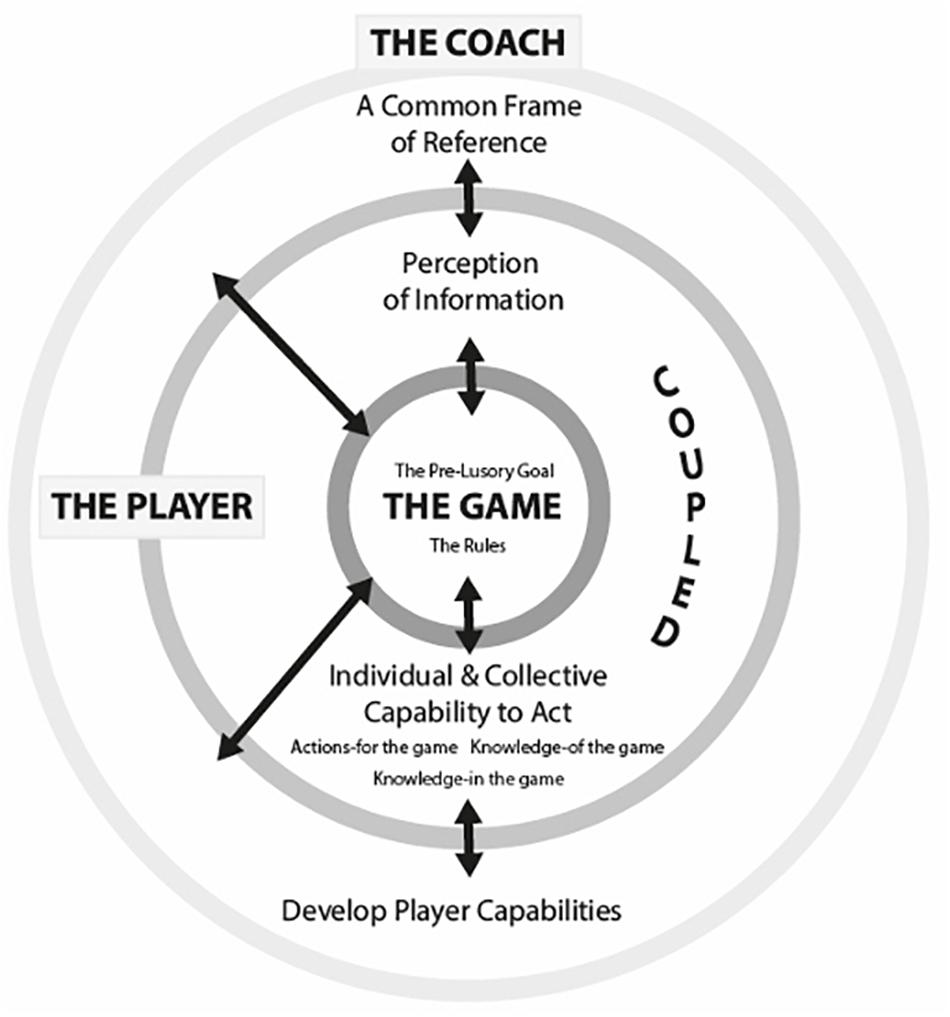
Frontiers | What Cognitive Mechanism, When, Where, and Why? Exploring the Decision Making of University and Professional Rugby Union Players During Competitive Matches

Fundamental Mechanisms of Regulated Cell Death and Implications for Heart Disease | Physiological Reviews
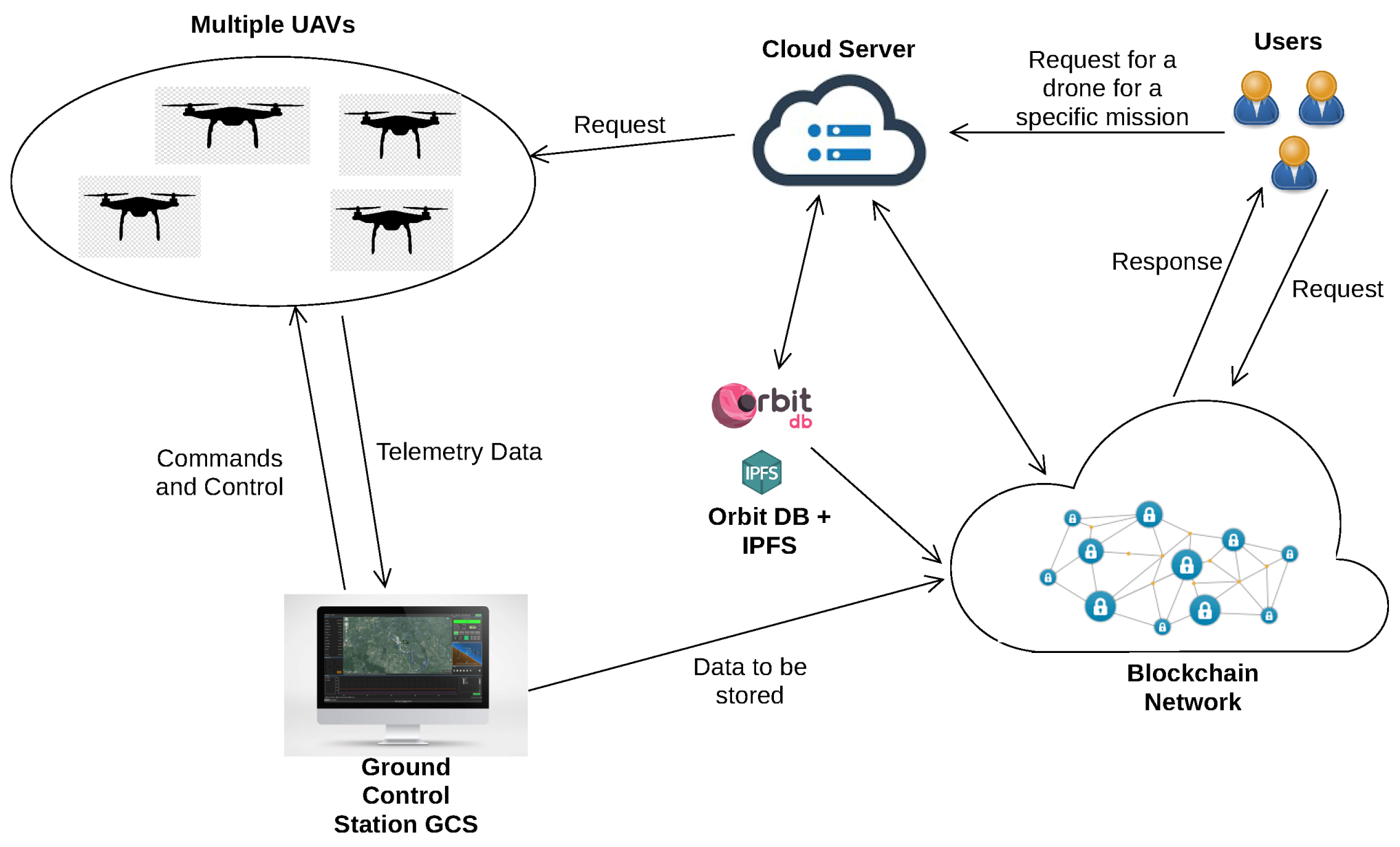
Sensors | Free Full-Text | UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones
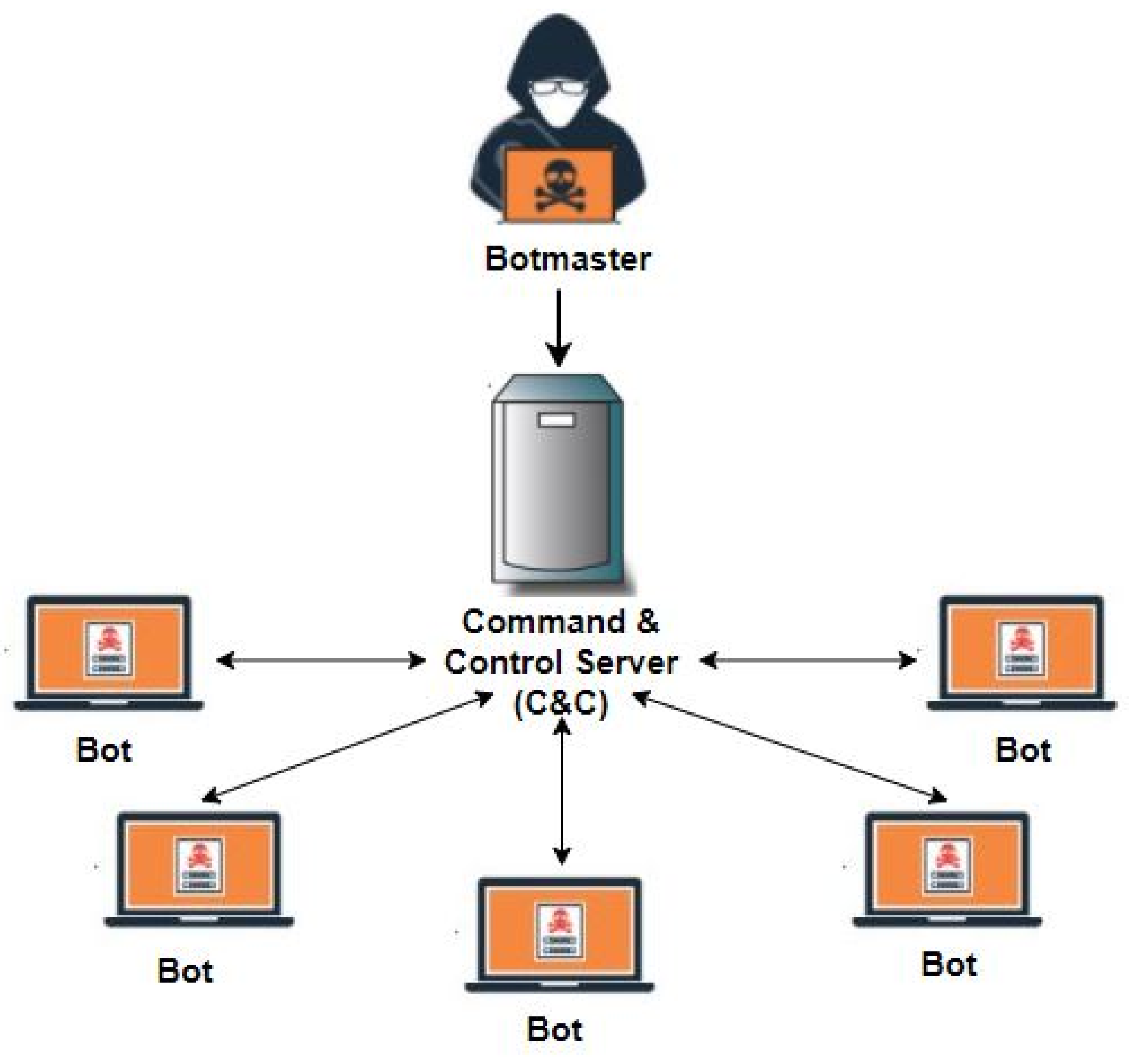
Symmetry | Free Full-Text | Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review