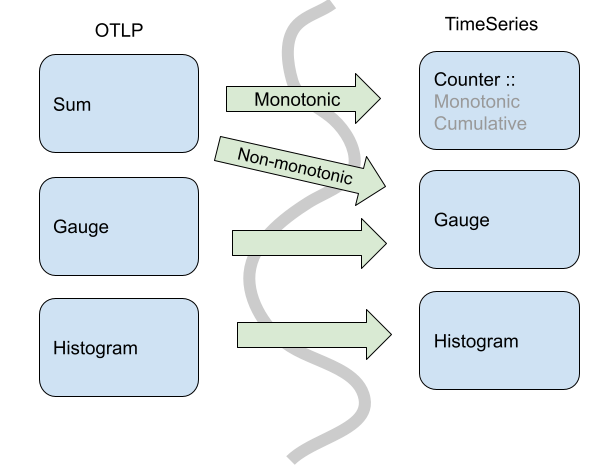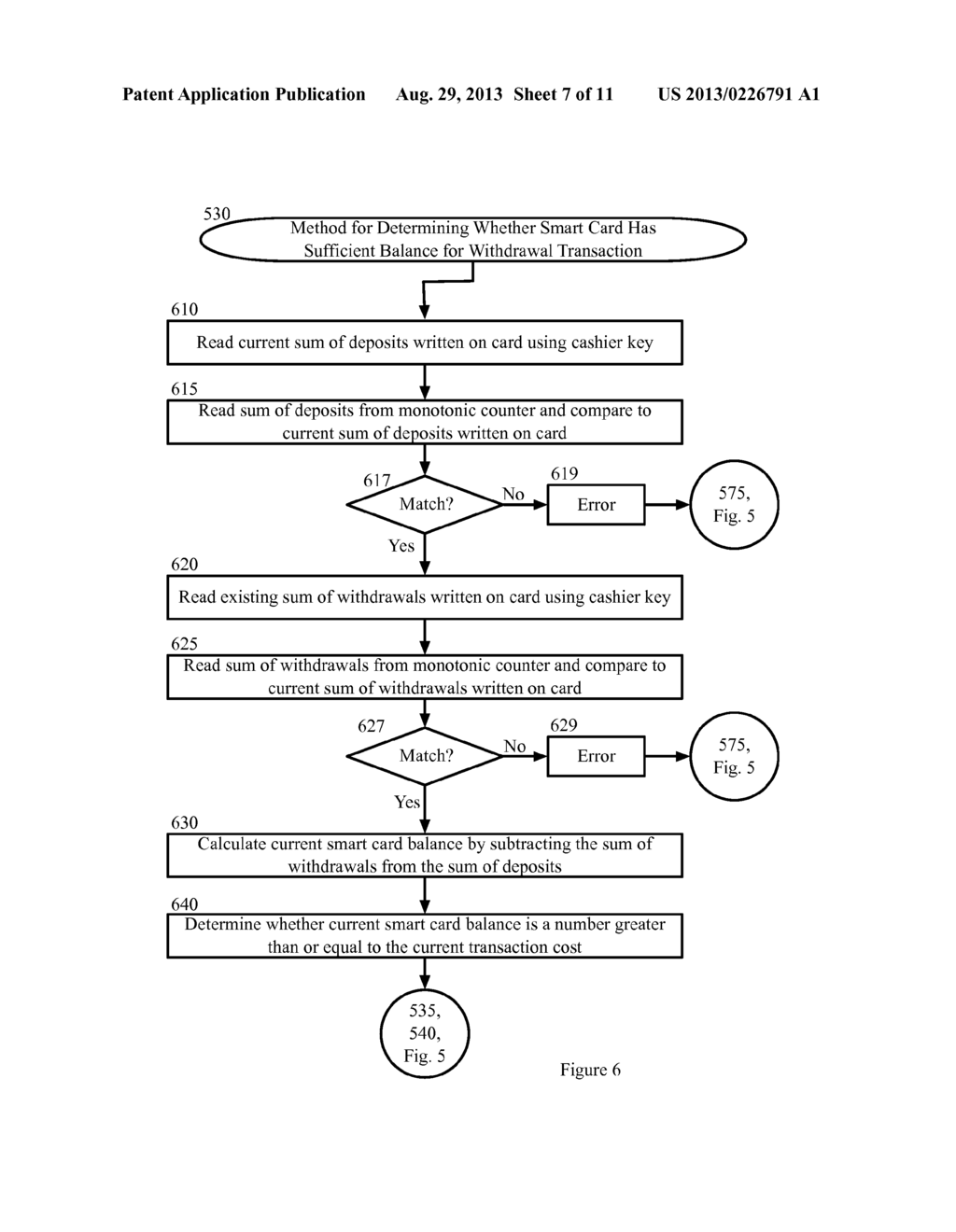
In-Card Access Control and Monotonic Counters for Offline Payment Processing System - diagram, schematic, and image 08
Virtual Monotonic Counters and Count-Limited Objects using a TPM without a Trusted OS (Extended Version)

TPM based Virtual Monotonic Counters and Count-Limited Objects without a Trusted OS ∗ | Semantic Scholar

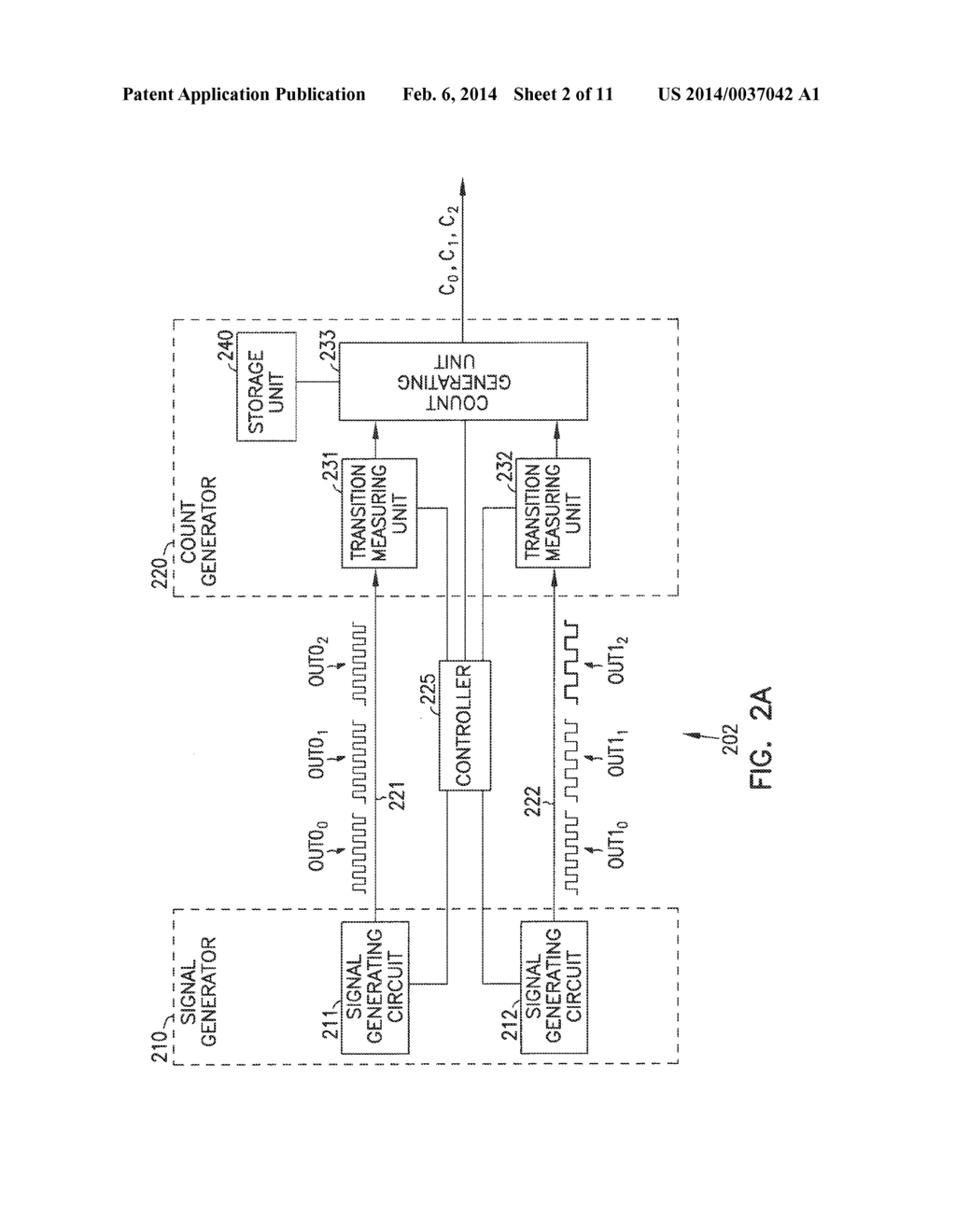
Figure 2 from Virtual monotonic counters and count-limited objects using a TPM without a trusted OS | Semantic Scholar
![PDF] Virtual monotonic counters and count-limited objects using a TPM without a trusted OS | Semantic Scholar PDF] Virtual monotonic counters and count-limited objects using a TPM without a trusted OS | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fc71807dd748cde9798f1b305bc58c1252b0d38/5-Figure1-1.png)
PDF] Virtual monotonic counters and count-limited objects using a TPM without a trusted OS | Semantic Scholar

Micron Unveils Serial NOR Flash Interface With Replay-Protected Monotonic Counter For Ultrathin Devices IT Voice | Online IT Media | IT Magazine

Virtual Monotonic Counters and Count-Limited Objects Using a TPM without a Trusted OS Luis F. G. Sarmenta Joint work with: Marten van Dijk. - ppt download


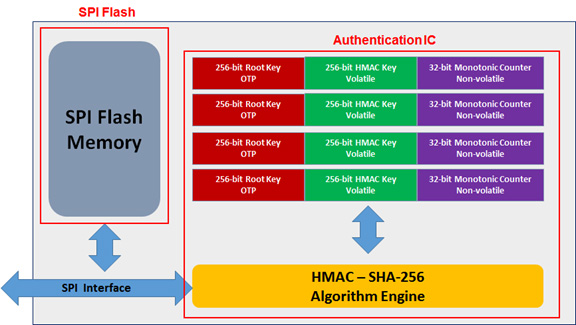

![PDF] Making Speculative BFT Resilient with Trusted Monotonic Counters | Semantic Scholar PDF] Making Speculative BFT Resilient with Trusted Monotonic Counters | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/04d0dde2fd959fbb65410def24b2bb2867cc0d53/4-Figure1-1.png)