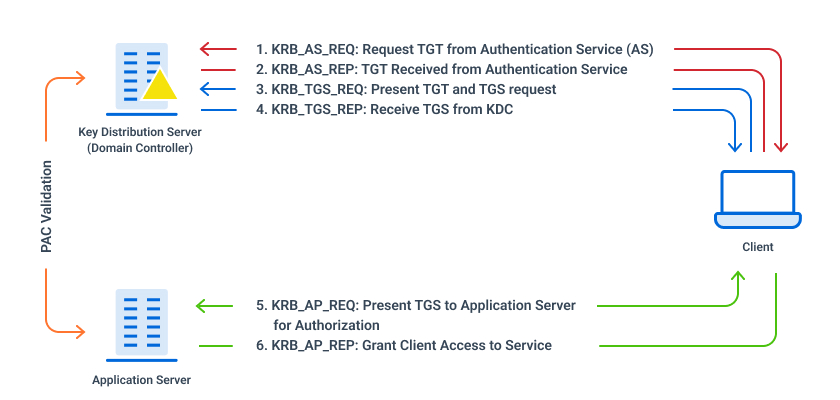
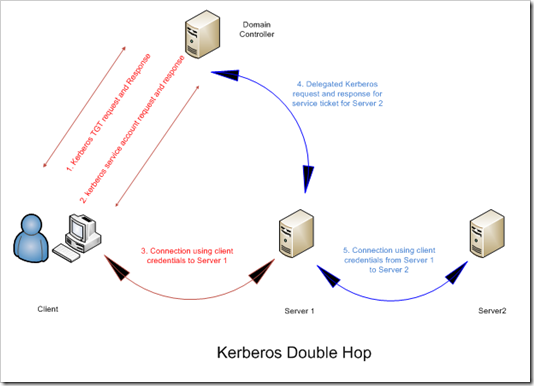
Preparing on-premises and AWS environments for external Kerberos authentication for Amazon RDS | AWS Database Blog
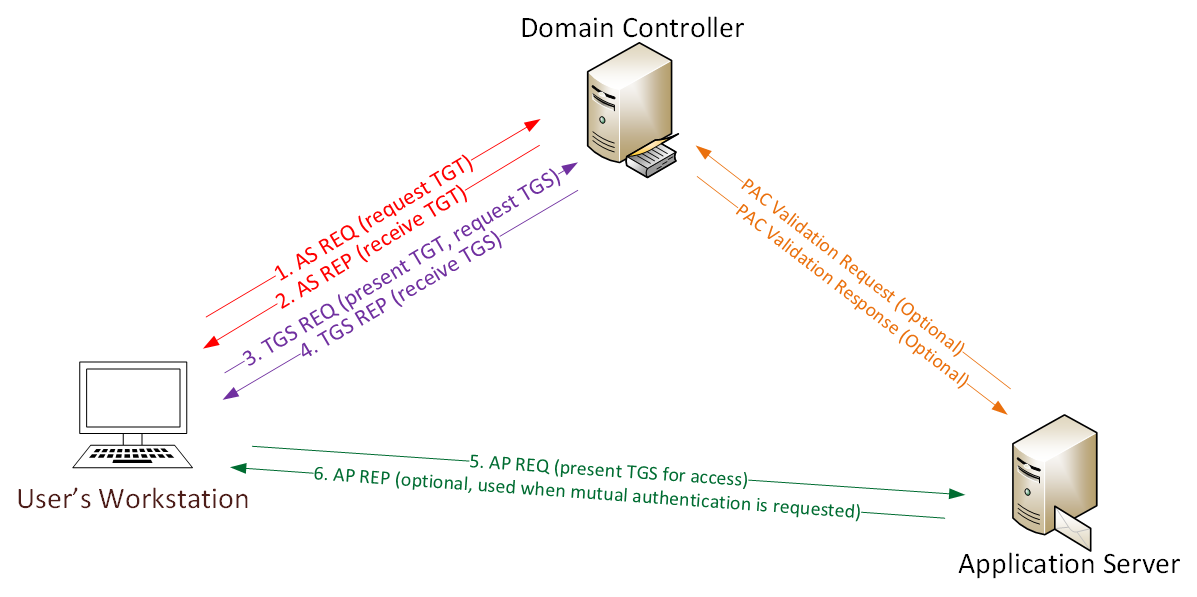
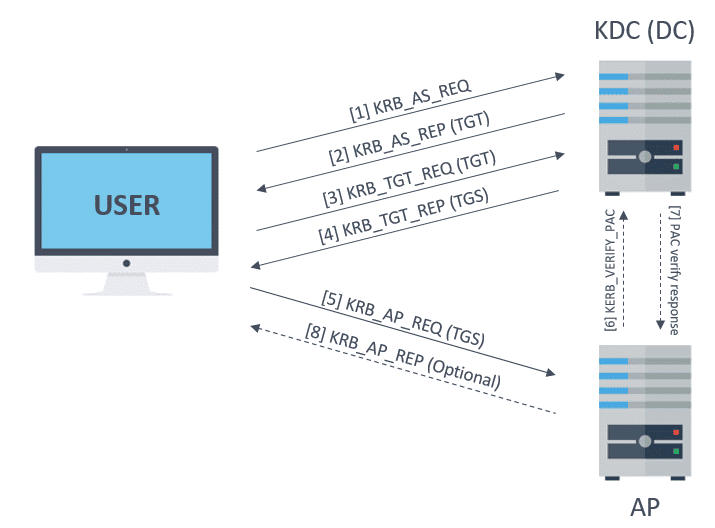
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory – Active Directory Security

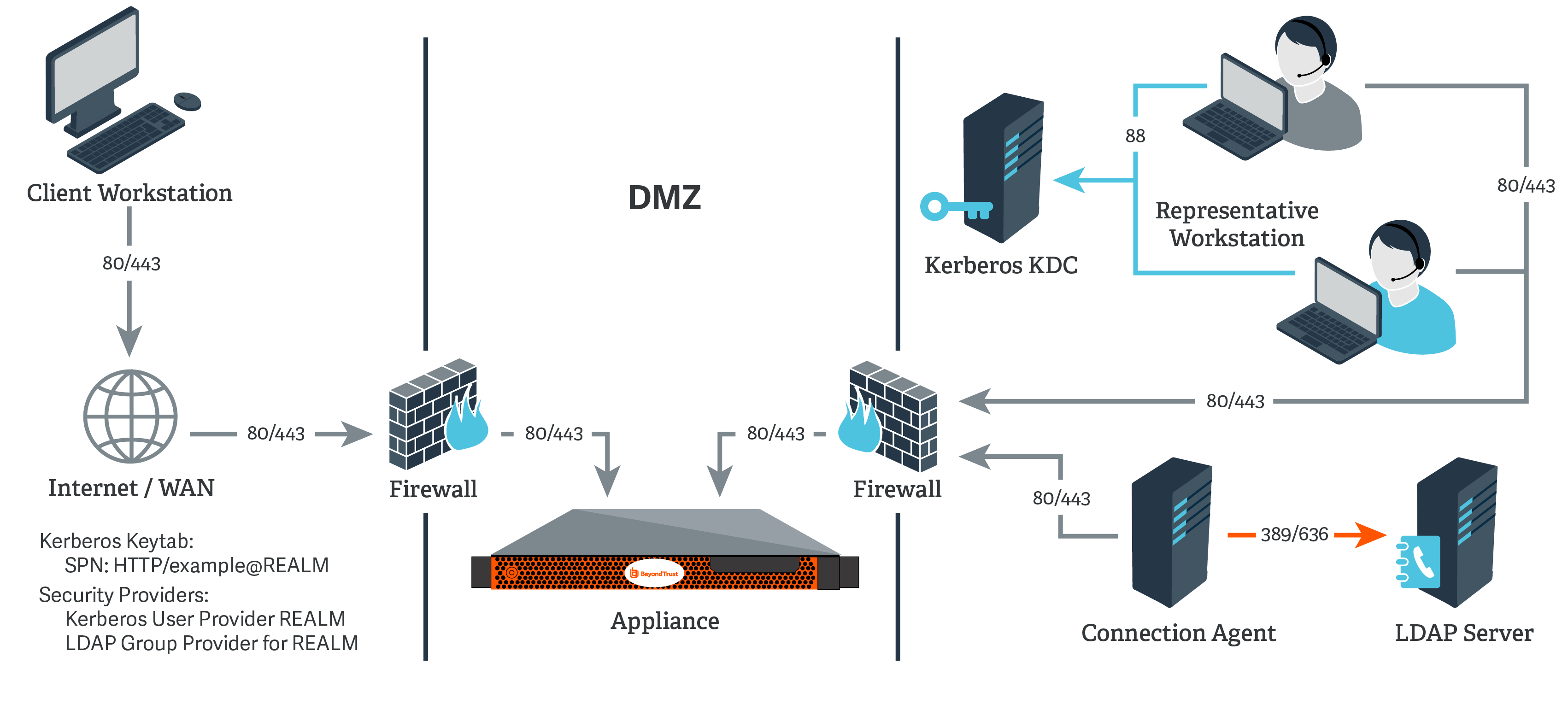
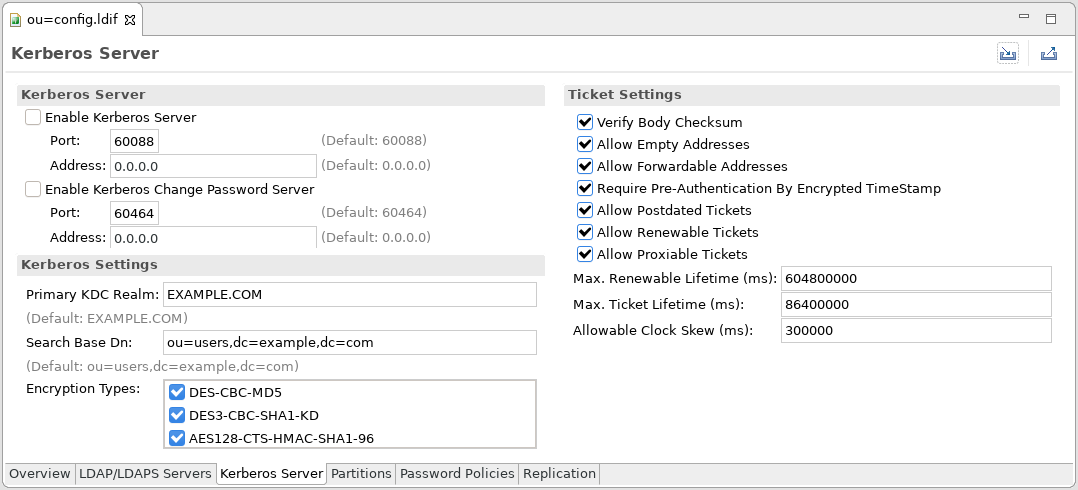
Novell Doc: Novell Access Manager 3.0 SP4 Administration Guide - Configuring Kerberos for Authentication
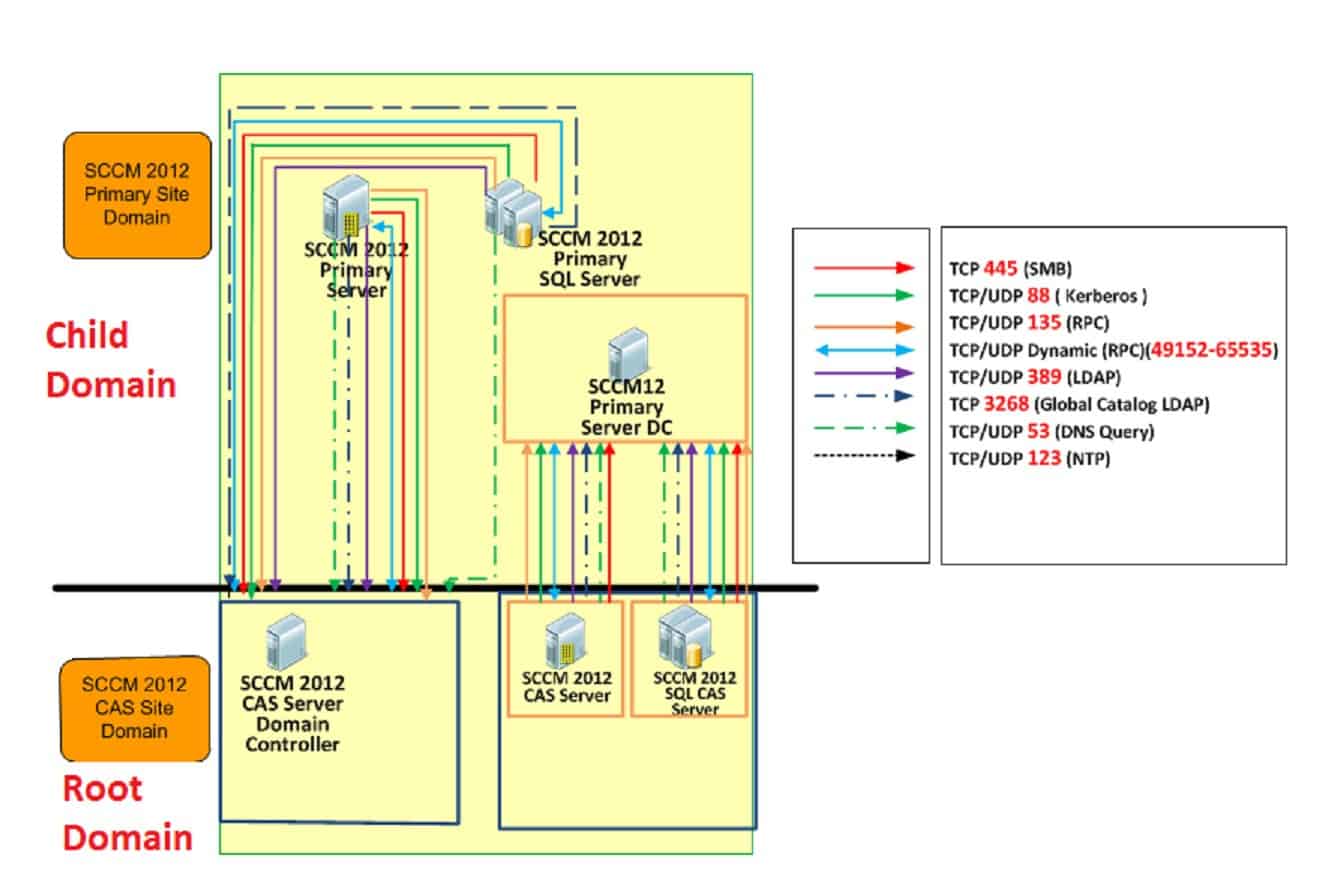
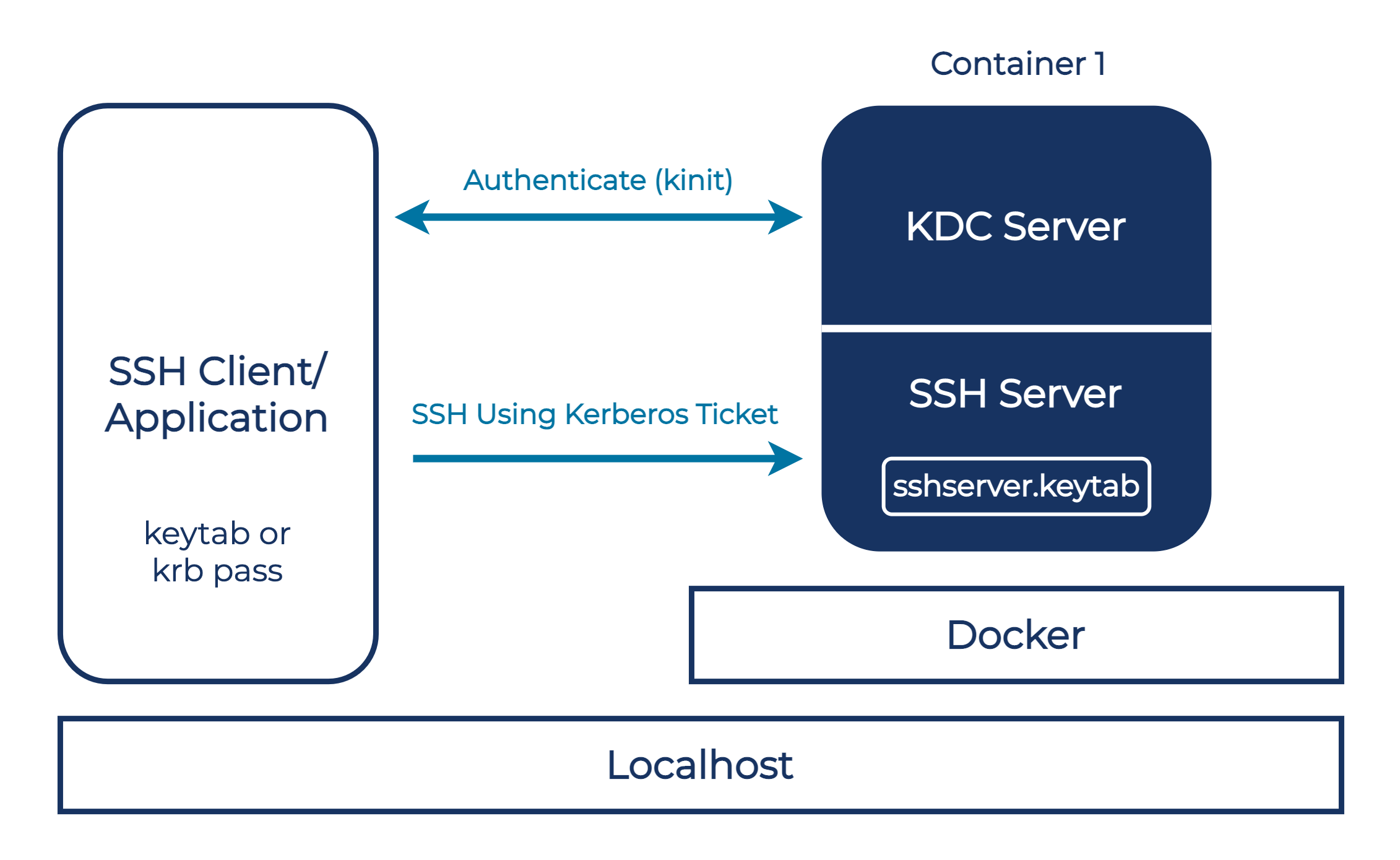
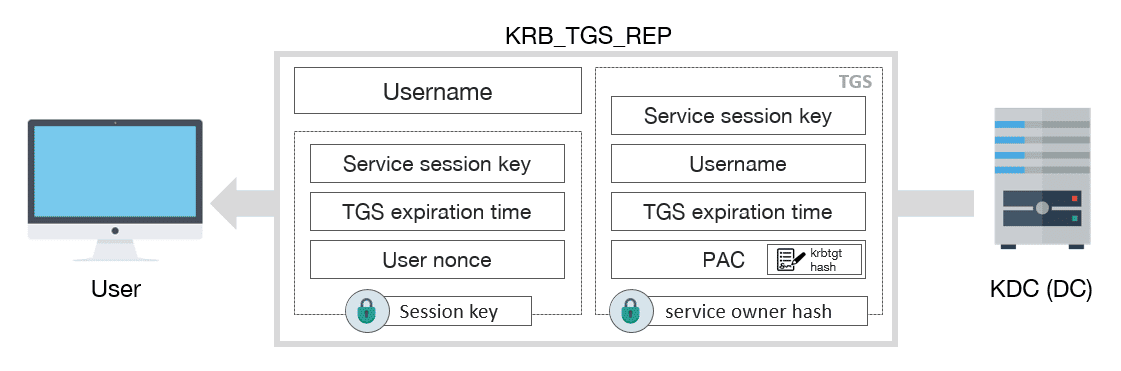


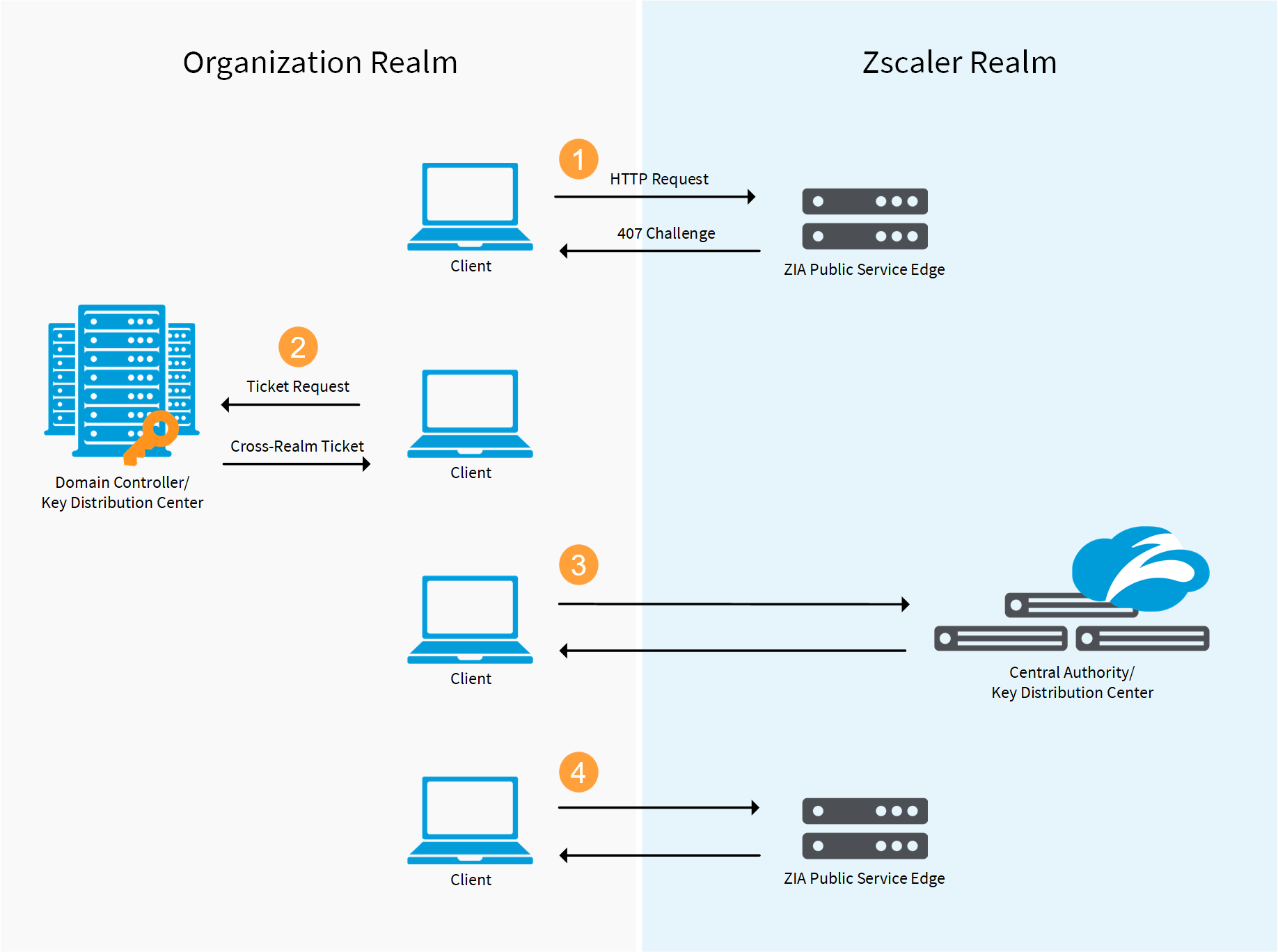

![Firewalls, NAT, and Kerberos - Kerberos: The Definitive Guide [Book] Firewalls, NAT, and Kerberos - Kerberos: The Definitive Guide [Book]](https://www.oreilly.com/api/v2/epubs/0596004036/files/httpatomoreillycomsourceoreillyimages2077824.png)